Phishing. No, not the outdoor activity that takes places along a river, but an electronic communication disguised as a trustworthy entity with the intent to obtain sensitive information or data from others.

We’ve all heard of the term, but what does it mean, what do they look like, and how can we avoid falling for them?
The term does itself comes from the analogy of an angler throwing a hook with bait, and hoping you bite. Translate this into a computer format, and attacks normally come in the form of an email (sometimes text messages) pretending to be from a popular provider or familiar contact, and encouraging you to click on a link.
It’s not a new problem though, if anything the oldest as it dates back to the early 1990s, however it has continued to evolve as the techniques used become more clever. Crucially, as computers get faster, so does that of the fraudster too. In 2019, nearly 1/3 of all security breaches involved phishing – off the shelf tools and templates are making this easier and easier.
How does it typically work?
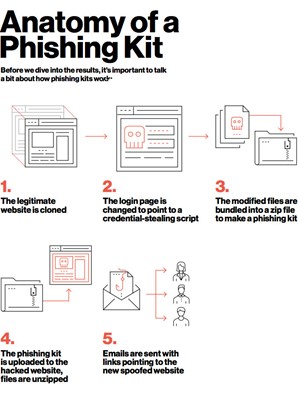
The following methods are perhaps the most common at the moment, and with the right knowledge is remarkably simple.
Copy a website -> adjust the login page scripts to steal credentials -> package these scripts -> insert back into a hacked website -> send out emails to users with link to new website
- Company using Office 365 for data and emails – easy to send an email pretending to be from Microsoft, and trick people into giving their details over
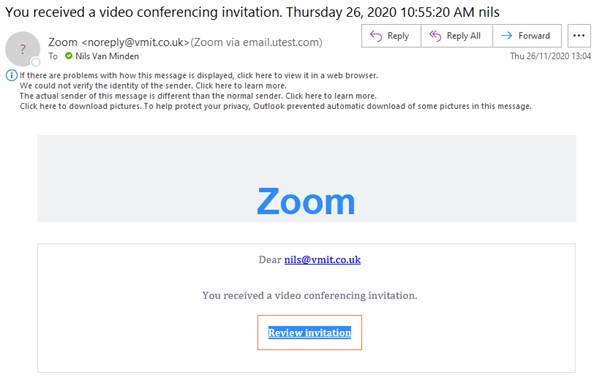
- Worldwide pandemic where everybody starts using Zoom – a great opportunity to pretend to be Zoom or a loved one inviting you to a meeting, and again give out details
What is the object of the attack?
The object is quite simple – to obtain your data and potentially money, by getting you to hand over your details
An email will be sent to multiple email addresses with a malicious link. As soon as you click on the link it is likely tracked – they know that you are interested, and have fallen for an email they have sent
You enter in your email address and password – they have confirmed your email address, and the password to that account.
If there is no Two Factor Authentication (2FA) on that account, they then have access to your email account. From this they can work out other websites you are connected to. Assuming your password is the same on other websites, and again no 2FA is present, they can login as you and purchase/transfer money etc.
Whilst only a small percentage of users will fall for a phishing email (if their spam filter hasn’t picked it up already), remember that the majority of phishing emails will be sent to millions of email addresses. Even a 0.01% success rate on 1million emails is still 100 users
Can you spot a phishing email?
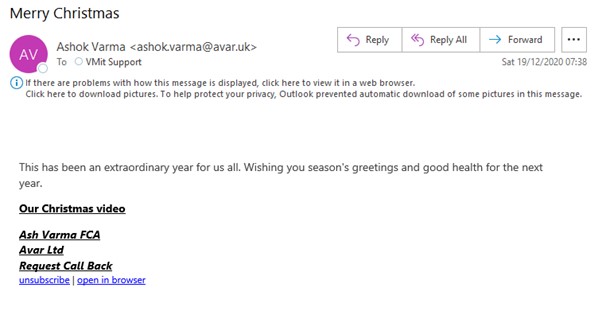
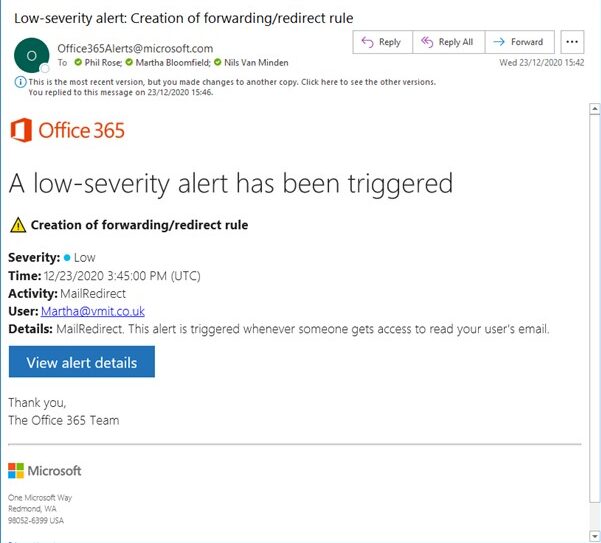
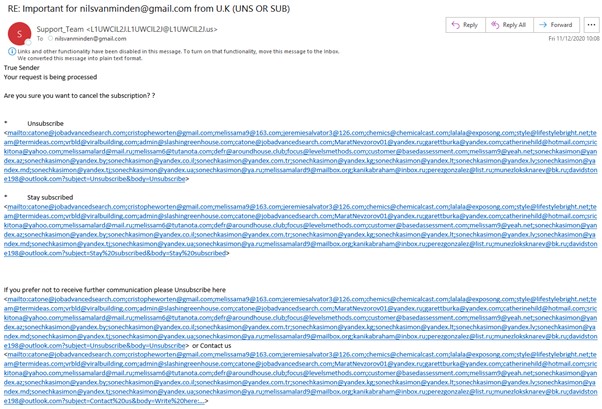
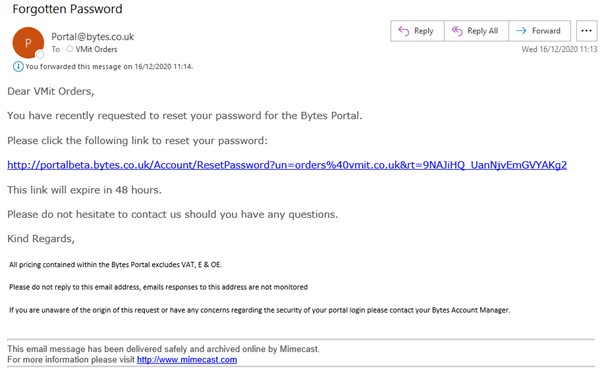
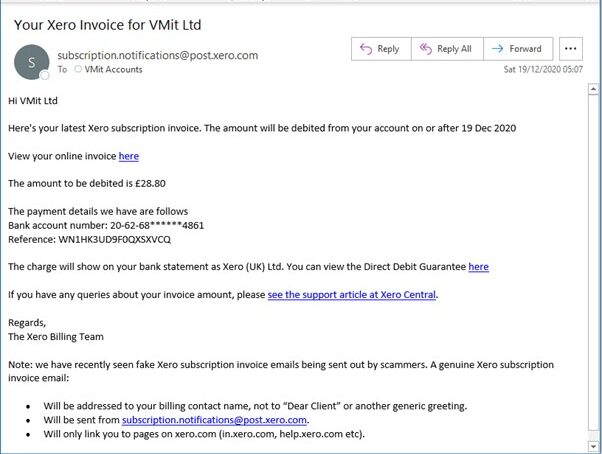
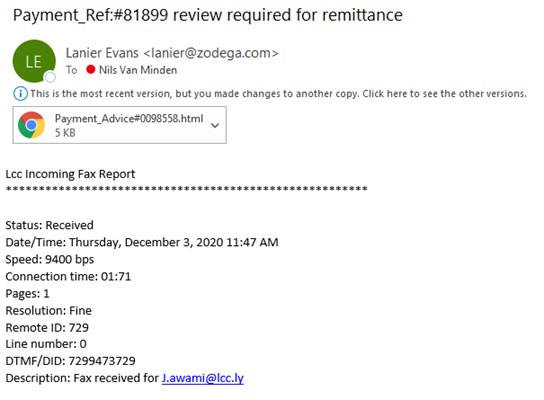
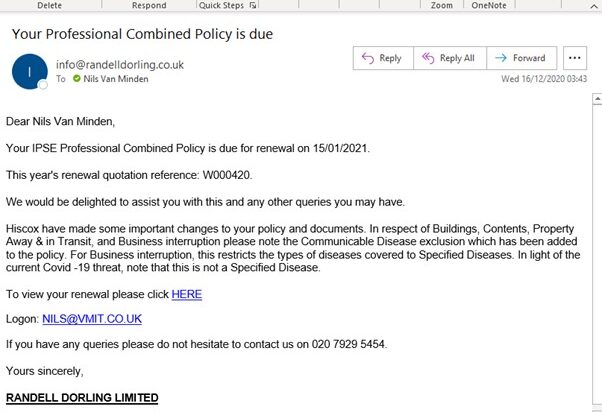
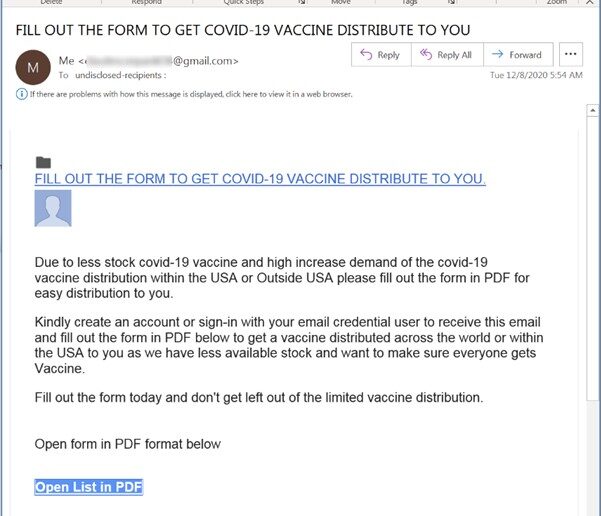
Look at the following examples we have received over the past few months, and see if you can identify which ones are genuine or not. Answers are at the bottom of the page
How can we tell if it is genuine or not?
They say that a police officers nose can detect trouble from afar, and we wish it was that simple to detect a phishing email too. There are no hard and fast rules that apply to each email, as the line between genuine/fake emails can often be blurry.
So what can we do? Can we do anything?
How can we protect ourselves?
We wish it was possible to block all spam/phishing emails, but this would come at the cost of blocking genuine emails too. But follow our tips below, and you’ll be well on the way to preventing being a victim
- Remember that not everyone you talk to online may be who they say they are
- Don’t click on any links directly, what if their systems were hacked? Browse to the website manually and login there, to verify the claim.
- Phone the sender and check the request
- Educate and encourage staff to stop and question emails that seem unusual. Get them to check with others, and don’t make them feel this is a waste of time
- Have different passwords for different websites. We partner with Dashlane, and use the software ourselves, to make password management easier
- Apply 2FA wherever possible. Even if a password is obtained, they will not have the 2FA codes to login
- Remember it’s a moving parade – what a phishing email looks like today will not be the same tomorrow
The above steps go for emails received from VMit as well. If you receive an email from us that you are not sure of, do contact us using the number you have on records rather than the one supplied in the email to verify it is genuine.
What are our providers doing about it?
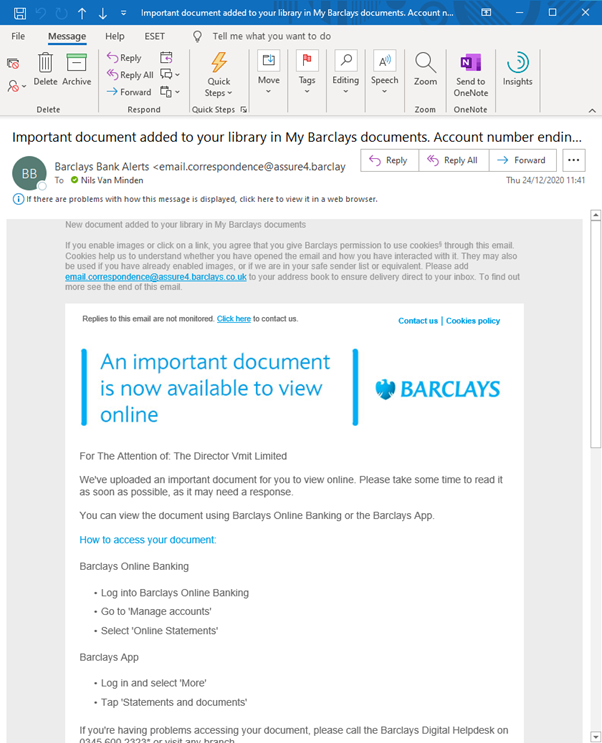
We received the following email from our bank, alerting us to a document to view online.
Rather than just giving users a hyperlink, straight away Barclays are advising users to head to the website (or their phone app), and access the document. This is exactly the way it should be done
And the answers?
- Spam – email from different source, and was unexpected
- Genuine – although still don’t click the links straight away
- Genuine – although formatted differently to most Microsoft emails, verified by checking with staff
- Spam – email address very unusual
- Genuine – we verified by checking with staff
- Genuine – verified by logging into website directly
- Spam – unexpected, small attachment, unknown sender
- Genuine – verified by logging into website directly and having paper records
- Spam – poor English, and sounds too good to be true