ASAP. ISP. LASER. PIN. NASA.POTUS. ATM. HTTP. JPEG. RAM. CRT. LCD. ADSL. USB. 2FA. SMS.
Now be honest, how many of those have you come across or know what they mean? The truth is, our modern world is full of acronyms, and it’s not just teenagers using them.

What does 2FA mean?
2FA is short for Two Factor Authentication. Put into action, 2FA means that when logging into electronic applications such as websites, you need 2 factors or ‘evidence’ to prove your identity.
You may have also heard of MFA, or Multi Factor Authentication, as an extension to 2FA – you need a 3rd or 4th bit of evidence!
What are the factors?
- Something the user has: Any physical object, such as a bank card or a key
- Something the user knows: Certain specific knowledge, such as a password or a PIN
- Something the user is: A physical characteristic, such as a fingerprint, voice or eye iris.
- Something the user does: For example, the speed or pattern of key presses
- Somewhere the user is: Location of the device, such as the computer network or GPS signal
To be a true 2FA method, the types of identification must differ. For instance, a password and a PIN would not fit this criteria, as they both rely on something the user knows.
Why use 2FA?
Whilst using a password to enter a website/application has been standard place for many years, so has the number of websites and information we store on our computers. Computer power has also grown exponentially in the same period.
With only 1FA in place (just the password), asking a computer to try lots of different passwords is not onerous or difficult for a cyber-criminal to achieve. Remember, they only have to be correct once and they have access to your account. However, the more authentication methods you have configured on your accounts will significantly reduce the chance you will become victim of this.
2FA in the real world
A good example of 2FA already in action is the way we withdraw cash from an ATM, or pay for things. Only the correct combination of a bank card (something you have) and a PIN (something you know) allows the transaction to be carried out. *
Sticking on the bank theme, when accessing your online banking, on top of your password (something you know) Barclays introduced their ‘PINSentry’ device, or Lloyds Bank request that a text message (SMS) to your phone – both containing a code that only works once (something you have)

* We realise since COVID-19 and the wider adoption of contactless cards, this example is now a little outdated! This is why there is a limit on the value of contactless purchases, or you have to enter the PIN every so often – to mitigate the reduction of security to 1FA.
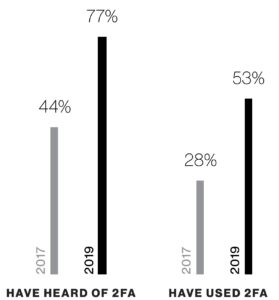
Businesses and 2FA
Knowing that our digital lives, both personal and business, are stored in a digital way we shouldn’t be asking “why do businesses need to add 2FA” but “why hasn’t 2FA been configured already”? Just some reasons why we believe that motto:
- Prevention is cheaper than recovery, both in data recovery and reputation costs
- 2FA cannot prevent every attack, but it is very effective against remote attacks
- Once configured, the daily login process for trusted devices is no slower than before
- There is no licensing cost, at all
- More and more websites support 2FA
At VMit we practice what we preach and configure 2FA on every online account that we hold and has the ability to be configured. We also use the Microsoft Authenticator app on our phones, again as a more secure method than just sending a text message.
How to configure 2FA
To list the process for every online platform or website would be an exhaustive list. However, we recommend that at a minimum every business configures 2FA for all their Office 365 accounts, and where possible using the Microsoft Authenticator app. Click here to find out how to achieve this.
https://docs.microsoft.com/en-us/microsoft-365/admin/security-and-compliance/set-up-multi-factor-authentication?view=o365-worldwide
Why not contact us today to walk you through this process?
Is 2FA foolproof?
As mentioned earlier, employing 2FA is not able to stop every type of attack, but it’s a big step in improving your overall security portfolio. Unfortunately, the weakest link is often the human element. For example:
- A cyber-criminal has your password, and a 2FA request comes through to your landline or mobile phone. Blindly accepting it when you are not expecting the request has let them access your account
- A phishing email comes into your mailbox and you click on the link in the email. This installs a rogue application that then captures & uploads your data, without logging into your account
Backups
For both of the reasons above reasons, it is important to remember that 2FA is not a replacement for backing up your computer or your email account to an alternative location, such as Acronis. Click here to find out more about Acronis
It is also important to remember to backup your codes, or have a recovery method configured. Why? Those mobile phone transfer tools do not transfer the 2FA codes, and if you then dispose of the old phone you can find yourself locked out!
The answers!
ASAP: As Soon As Possible
ISP: Internet Service Provider
LASER: Light Amplification by Stimulated Emission of Radiation
PIN: Personal Identification Number
NASA: National Aeronautics and Space Administration
POTUS: President Of The United States
ATM: Automated Teller Machine
HTTP: HyperText Transfer Protocol
JPEG: Joint Photographic Experts Group
RAM: Random Access Memory
CRT: Cathode Ray Tube
LCD: Liquid Crystal Display
ADSL: Asymmetric Digital Subscriber Line
USB: Universal Serial Bus
2FA: Two Factor Authentication
SMS: Short Messaging Service

